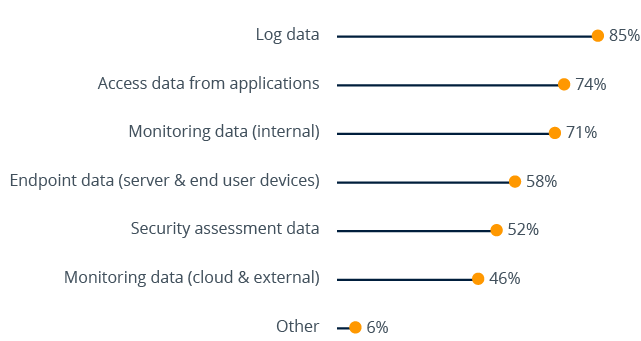
Sources of raw security data used for analytics (n=202)
The most prevalent source (85% of respondents) is system and application logs. Log files are often kept not only for security analysis, but also for reasons such as compliance and auditing. However, the survey results show that a range of other data sources are being widely used. Nearly half of our survey respondents have even gone as far as integrating external threat intelligence and cloud service monitoring data into their security analysis.
Of course, this does not necessarily mean that all of them are able to correlate their security information across multiple sources – some may still rely on standalone security solutions while others are running traditional Security Operations Centers to support manual forensic analysis of their security data. This is where the deployment of a big data security analytics solution would bring immediate benefits by reducing the number of security events from thousands to maybe dozens, labeled with a clear risk score and enriched with contextual information to simplify forensic investigations.
Big Data and Information Security Report
How big data technology can help to increase cyber attack resilience by better detection of attacks, enabling real-time response.
Request the free report now





