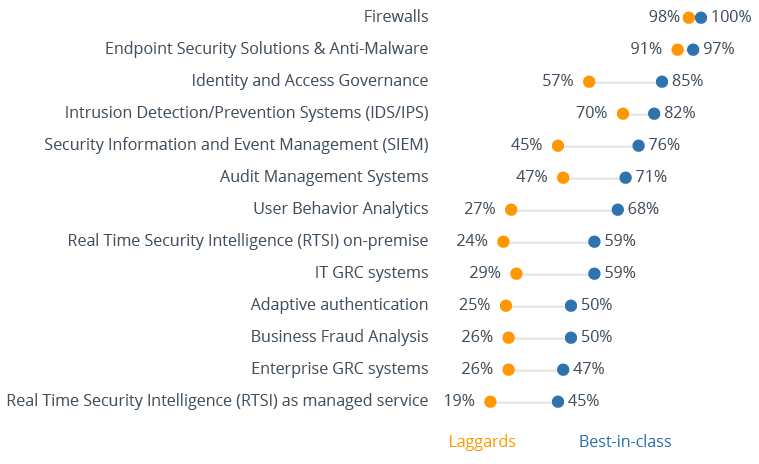
Security technologies used by organizations
Companies that closely follow the latest technological developments in the field of information security as well as learn about new types of cyber-attacks have a clear understanding that only a multi-layered and well-integrated security architecture is capable of protecting their assets from multiple attack vectors. These companies are deploying various security tools not just for threat detection, but for identity and access governance, strong authentication, security information and event management and, last but not least, security analytics. They rely either on traditional SIEM tools or modern RTSI products to obtain a single pane of glass visibility into all types of external and internal threats within their networks and thus can respond to those threats quickly and according to established workflows.
Unfortunately, other companies are still lacking the competence or budgets to design their security infrastructures that way. Most still rely exclusively on traditional perimeter security tools such as firewalls and endpoint protection products such as antivirus software to fight off hackers, which nowadays, when the very notion of a security perimeter has almost disappeared, is no longer sufficient, to say nothing about the complete lack of protection against malicious insiders.
Companies that currently do not employ any kind of protection against insider threats must urgently reconsider their security strategies and switch from the outdated perimeter-focused approach towards the modern focus on detection and response to threats within their corporate networks. To do this efficiently, companies must collect both historical and real-time security events from different sources across their IT systems and networks and perform a centralized analysis of this data to identify malicious activities.
Big Data and Information Security Report
How big data technology can help to increase cyber attack resilience by better detection of attacks, enabling real-time response.
Request the free report now





